Forum Replies Created
-
AuthorPosts
-
in reply to: Running inside a container #17019
Yes. HAast fully supports containers. Normally HAast will run inside the container with Asterisk; however, we have seen deployments where HAast runs on the host and starts a container (containing Asterisk) on demand.
If this is you first exposure to HAast we recommend installing HAast inside the container with Asterisk (and optionally a GUI).
in reply to: Do you support IPv6 #16972All of the libraries and components used by HAast are IPv6 capable, and HAast is designed to accept IPv6 settings. However, due to lack of customer demand IPv6 functionality is not currently tested or certified.
You are welcome to try IPv6 settings with HAast and everything may work. However, we do not officially support IPv6 yet. As of May 2022 we have not had any customer need IPv6 (though a few customers have inquired).
If IPv6 is essential for your implementation Telium would undertake a (for fee) project to certify HAast (only the platform and architecture of HAast you are using). There is not enough overall demand to justify doubling the entire QA process indefinitely for IPv6.
If you are an OEM or volume license customer please contact your account manager to discuss your needs.
in reply to: Move license between AWS servers #16835You have described two very different needs in your question, so I’ll try to answer them separately. If you choose Hardware Fingerprint activation on AWS, then your license is tied to your instance ID and MAC address. So you can safely move the instance between hosts (i.e. hypervisors, not guest VM’s), change instance size, etc. The license will remain activated (tied to that instance). You can safely start/stop the instance, just don’t ever delete it or delete the NIC as that will invalidate your license.
If you plan to have multiple AWS instances ready to start but will only use one at a time, then you should choose Cloud activation. Cloud activation is not tied to any (virtual/physical) hardware so whichever instance is running is the one that will use the license. However, do not start more than one instance at a time (i.e. don’t try to use a single license on multiple instances simultaneously) or that will invalidate your license.
I should point out that we use a third party license product, and they have no obligation to issue a new license once an existing one has been invalidated. In other words, if you invalidate your license you will most likely have to buy an entirely new license (full price). So plan your deployment carefully to avoid wasting a license. We have no ability to “un-invalidate” a license – we are at the mercy of the license vendor, and we understand their need to prevent license fraud as that’s the only way they can stay in business.
in reply to: Encryption of config file passwords #16546There are a few ways to address your problem.
First, you can limit access to the HAAst config files (or even entire /etc/xdg/telium directory) so that only the root user can read them. Using the chmod command will allow you to set these files to readonly (r – -) for root:
chmod 400 haast.confSecond, you can also encrypt the password before placing it into the config file. For example, using md5sum we can generate a hash of your obvious password:
[root@qa14 dev]# echo "MyObviousPassword" | md5sum 7f1e7328e9c668dbc73485eecd91b7ba -Then you would use 7f1e7328e9c668dbc73485eecd91b7ba as your password entered into the haast.conf file on both nodes.
Third, you can store sensitive config file information in the HAast keychain. To use a keychain value in a configuration item simply replace the value with @KEYNAME. Applicable configuration items show @KEYNAME as an option in the documentation. Note that a KEYNAME can contain only letters, numbers, and underscore, and case of the letters is ignored. See section 3.1 of the installation guide (as of Jan 2021) for further details of the keychain.
in reply to: Configuring second FreePBX node using HAAst sync #16504No! Unlike most of the other configuration generators, FreePBX does something a little unusual. Every time you add a module (or even upgrade a module) to your system FreePBX might change the structure of the database / add tables to hold the additional data.
So if you now sync from your primary node to your secondary node, settings would be lost because the associated tables/fields are missing on the secondary node. Conversely, if you now sync from your secondary node to your primary node, settings would be missing because the necessary source settings are absent. (See image below). This is why the HAAst installation guide and maintenance manual provide specific installation/upgrade instructions relating to FreePBX. Every year we have at least one customer that damages their FreePBX cluster because they did not follow the installation/maintenance guides.
Similarly, updating a module might change table structure, and that’s why we say to disable any automatic updates in FreePBX. Most other configuration generators are smart enough to detect a configuration mismatch between versions/modules, but FreePBX does not and will probably break (dialplan failure) unless the two nodes are kept identical (in terms of modules enabled/installed/versions).
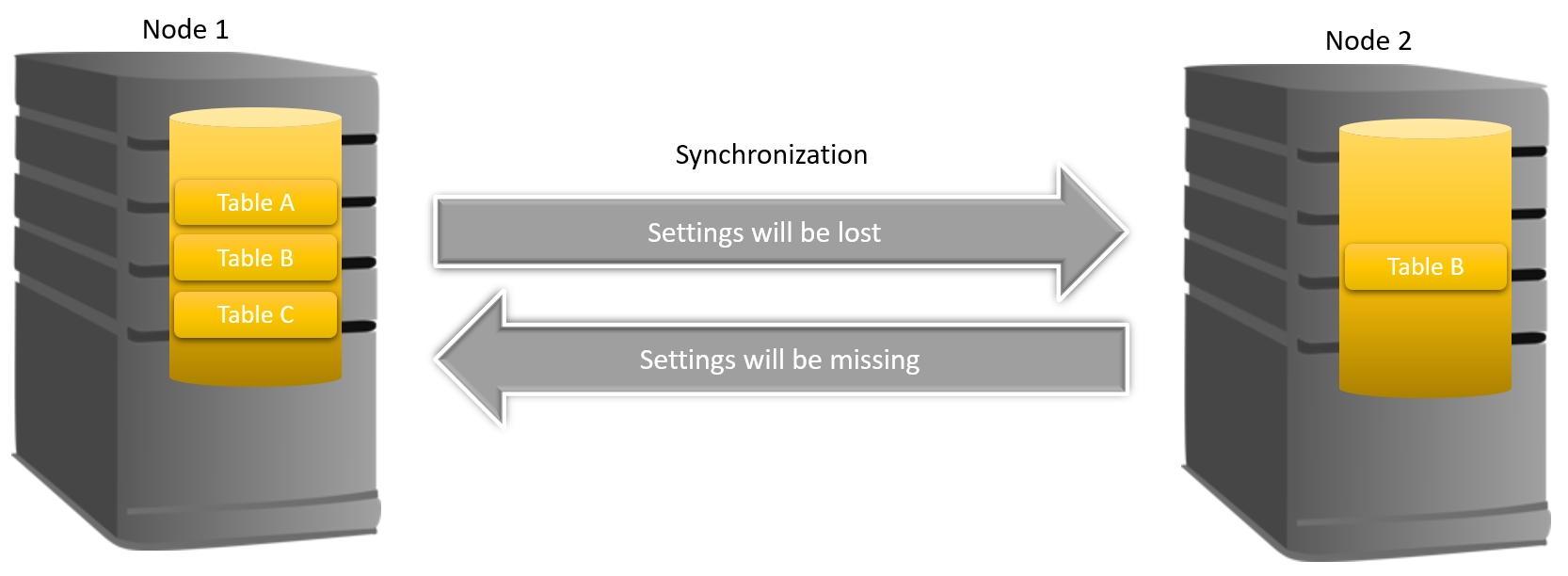
Even if HAAst were to copy the metadata (table structure) as well, you would still have problems since the PHP code which makes up FreePBX will not understand the settings (if the code version doesn’t match the settings version). This may result in the PBX failing to process calls as the dialplan crashes, and/or failure to configure, and/or failing to complete an APPLY button push.
To read more about how to properly setup your nodes with FreePBX see sections 3.6 and 10.1.5 of the Detailed Installation Guide, and sections 7 and 8 of the Maintenance and Operations Guide.
If you have already corrupted your FreePBX setup and your cluster won’t process calls (due to dialplan fialure) see this forum post
in reply to: Minimum hardware requirements for HAAst #16418HAAst is written entirely in C/C++, so it is highly efficient with a minimal footprint. Since HAAst runs on the same hardware platform as Asterisk, we cannot describe HAAst’s minimum requirements in absolute terms (since HAAst alone on a server makes no sense).
However, if you have a properly sized server (for the target Asterisk volume), HAAst will consume:
- Maximum 2% of available CPU
- 400MB of memory (in use, not swapped)
- 50MB of disk storage
In case you meant from a hardware compatibility standpoint, HAAst can run with many different CPU’s and system boards/chipsets. Since HAAst communicates with the system board to determine health, check with our support team if you are using a non X86/X86_64 standard PC motherboard. As well, releases for non-X86/X86_64 CPU’s are targeted at specific processors for optimization/power management reasons, so please check with our support team for the specific CPU you are targeting.
For more information see FAQ 1070
in reply to: Delay HAAst start on bootup #14370Since Red Hat 8 uses SystemD, the best way to delay HAAst start is with a service timer. Create the file haast.timer in the /etc/systemd/system directory with the following contents
[Unit] Description=Delay HAAst start by 1 minute on bootup [Timer] OnBootSec=1min Unit=haast.service [Install] WantedBy=basic.targetThen, enable the HAAst timer and disable the service:
systemctl enable haast.timer systemctl disable haast.serviceAnd finally, in your haast.service file change the WantedBy line to read:
[Install] WantedBy=haast.timerNext inform systemd of your changes:
systemctl daemon-reloadAnd your HAAst start will delay by 1 minute on bootup. You can adjust the delay as you need.
in reply to: FreePBX crashing on SIP attack #14340You don’t mention the version of FreePBX you are running but we can guess the cause; based on the timing of your message we are aware of a particular corrupt SIP packet attack which appeared in June 2020.
Please upgrade your SecAst to version 1.7.1 and your system will no longer be vulnerable to this attack. If you want want to send us detailed Asterisk/SecAst/Firewall logs we can help you confirm the cause and the resolution. (Please send by email, don’t post in the forum)
in reply to: Qt_5 not defined #14335This error is the result of incompatibilities between the Qt library expected by SecAst, and the Qt library installed on your system (or possibly because you are missing the Qt library altogether). SecAst version 1.7.0 is built against Qt version 5.9.8, so that is the library version you should install (at this date).
There is often a gap between the Qt version we use for a software release, and what is available across all Linux distributions / repos. (Each distribution / repo makes a slightly different version available). This problem should resolve itself once the repos catch caught up. Note that even version 5.9.8 is many releases behind the most current Qt version, so we are staying well away from leading edge.
As of July 13 2020 the Qt library available from Ubuntu 18’s official repos is 5.9.5. If you are a customer with a SecAst maintenance agreement we can build a release for you using Qt library 5.9.5 (or whatever version you need) at no charge. If you are using the free edition you can either wait (for your repo to catch up), or install the Qt open source libraries from: http://www.qt.io/download-open-source as those will always offer the very latest libraries
in reply to: How to view debuglog.tef files #14153Files with “debuglog” and “debuglog.tef” extensions contain diagnostic information to do with the operation of the services. (Eg: SecAst, HAAst, PBXsync, etc)
Files with “debuglog” extension are plain text, and you can view them in any editor or from the command prompt using the ‘cat’ command.
Files with “debuglog.tef” extension are binary files, (TEF stands for Telium Engineering Format). These files are read by our diagnostic tools to help diagnose a problem. You cannot view the contents of these files as you would require our engineering tools to do so.
in reply to: Which Asterisk distribution should I use? #14151Many configuration generators are trying to compete with one another on secondary features – covering everything from security, faxing, messaging, email, router, SBC, security, high availability, and more. Most users disable/ignore these add-ons as they can be poorly designed or integrated (the real strength of configuration generators is in managing the Asterisk configuration files). If you are planning to use their add-ons compare each carefully to stand alone products so you know what you are getting. (You may even find that a commercial module that you are buying is just a collection of open source packages).
Next there are more sophisticated PBX’s which use Asterisk as the media engine/call processing engine but extend the functionality using a variety of other programs. PBX’s like Amtelco’s Genesis / ISS fall into this category. Telium is also pleased to work directly with manufacturers of more sophisticated PBX’s suchs as Amtelco Genesis / ISS to ensure full compatibility and deep product integration.
And finally there are some ‘closed’ PBX’s which are Asterisk based, but according to their vendors they are not compatible with ANY add-ons (unless sold from that same manufacturer). In reality we have helped customers install HAAst/SecAst/and many other 3rd party products onto these systems. However, we don’t want to upset these vendors so we leave it up to the customer to determine if they can/want to reset the root password and install other products. (It’s your product, so you probably have a right to modify it as you see fit). But we don’t offer any assistance that might violate the DMCA in the USA, or similar laws in other countries. (e.g. you can find instructions on how to unlock/remove vendor protections on the internet, but we can’t give those instructions to you). Also if you are an authorized vendor of such closed systems read your reseller agreement carefully; your customer can do what he wants with the PBX but you might violate your reseller agreement if you unlock the box for them.
HAAst tries to work well with every configuration generator. We are pleased to add support for new products/databases, but we also deprecate support for little used configuration generators / databases / features. If you are a large corporation or critical call center using Asterisk directly (no configuration generator) then HAAst can fully support you as well. You don’t need a configuration generator or add-on to use HAAst, SecAst, etc.
So if you are designing a telephony solution we recommend:
- Pure asterisk (no configuration generator) if you are ok doing some basic diaplan coding
- If you need a configuration generator pick one that is fully open source (avoid anything with ‘distro’ in the name)
- Use flat-files to hold config information
- If you need a database (or your config generator needs a database) insist on MariaDB/MySQL
If you need to stray from this advice be sure to understand the compromises you are making
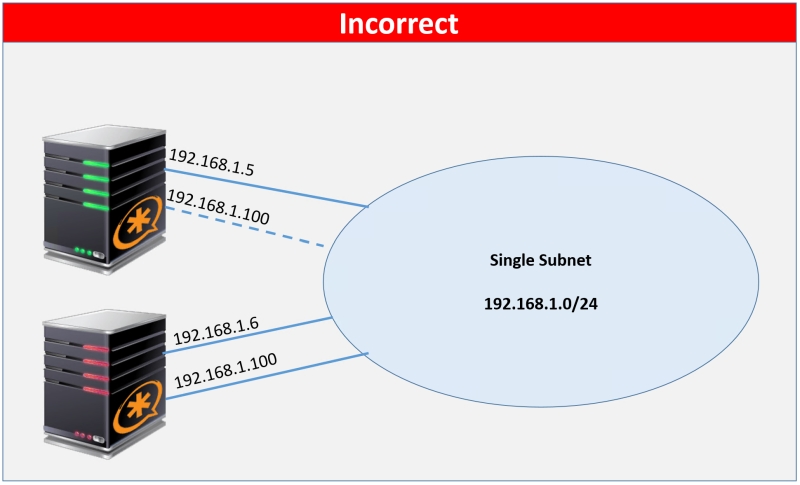
in reply to: How to configure IP for each NIC #14074The problem you are encountering has nothing to do with HAAst, and everything to do with the basics of networking. You have setup 2 NIC’s in each PC, but they are on the same subnet! That means that Linux has no idea where (out which NIC) to route traffic for your 192.168.1.0/24 subnet. You should not do this as it confuses Linux. This topic is part of what’s known as “multihoming”, and I would suggest you research this topic a bit further before you continue to setup your networks. As well, reread the HAAst installation guide – there’s a bit more information on this topic there. (This isn’t the first time we’ve seen this issue in the support group).
By shutting down NIC1 on either PC you allow Linux to figure out how to properly route, but then your management NIC is gone so the cluster fails over.
The solution (for 2 NIC’s per PBX) is to ensure that each NIC is on it’s own subnet. For example:
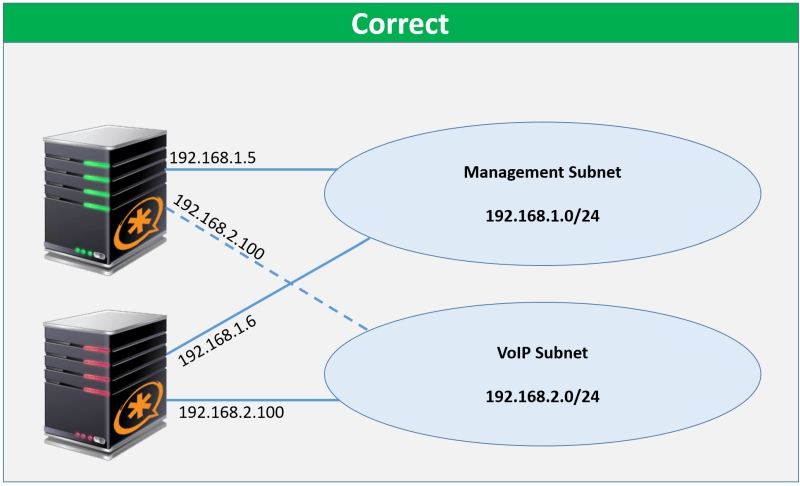
For advanced users only: It is possible to use a single subnet for management and VoIP, and move a shared IP address between nodes. However, setup is beyond the scope of included technical support (i.e. not officially supported). If you an advanced user and want to experiment independently, you can learn more here.
in reply to: Single subnet for management NIC and VoIP NIC #6858I should start by saying that we don’t officially support this design because some of the steps involved are beyond the skill of an average administrator.
If you are very comfortable with networking, iptables, and routing then the answer is YES this can be done. (But our support team cannot assist you further with this topic).
Suppose you have
- one NIC in each node
- a single subnet 192.168.1.0/24 (i.e. 255.255.255.0 subnet) used by each NIC
- Node A uses 192.168.1.1, and Node B uses 192.168.1.2
and you wish to have HAAst add 192.168.1.3 to the active node (while leaving the management IP accessible). The steps to do so are:
- Setup the OS to assign the static address 192.168.1.1 and 192.168.1.2 to their respective nodes
- Setup haast.conf to enable the VoIP NIC feature, and tell HAAst to use 192.168.1.3 as the shared IP
- Setup the HAAst pre-start event handler to add the following postrouting rules in the NAT chain to source-NAT all outgoing voice traffic (5060 + RTP ports) as the shared IP:
iptables -A POSTROUTING -t nat -p udp –dport 5060 -j SNAT –to-source 192.168.1.3
iptables -A POSTROUTING -t nat -p udp –dport 10000:32768 -j SNAT –to-source 192.168.1.3 - Setup the HAAst post-stop event handler to remove the above rules.
The end result will be that all voice related traffic will have their headers rewritten to show 192.168.1.3 instead of 192.168.1.1 (or 192.168.1.2). Depending on the VoIP protocols you use, TCP vs UDP selection, and other socket services you offer you may have to expand on or customize these rules. But the above should be sufficient to show how to accomplish what you want.
in reply to: Constant failover #6856If the Asterisk control file (wrapper) is exiting with code 3, that means Asterisk is taking too long to start. I recommend you disable the HAAst service and manually try to start the Asterisk service directly.
I suspect you will see a long and slow (or errored) start of Asterisk. The systemd service file included with Asterisk is not ideal for cluster use and can cause slow startup. If you are using systemd please try the service file offered by Telium here:
https://telium.io/topic/cant-start-asterisk-exit-code-158/
-
This reply was modified 4 years, 3 months ago by
WebMaster.
in reply to: Errors / warnings after sync #14329Note that Sangoma made a change to FreePBX in late-2019 (release 1904 or later) that could cause incomplete synchronization or other failure. We recommend that all customers using FreePBX with HAAst upgrade to HAAst version 2.5.9 or later to ensure critical issues are addressed. (Now even tables with invalid structures will sync)
For further details of updates and fixes please see the ‘changelog’ file included with the distribution package.
-
AuthorPosts

