Security for Asterisk
Security designed specifically for telephony
SECAST
»
TECHNOLOGY
Built for Telephony Security
Detects attacks unique to VoIP telephony
Integrates deeply with Asterisk to monitor user activity in realtime
Leverages massive database of VoIP specific hacker IP addresses and fraud related phone numbers
Offers ability to create responses unique to each attack using SecAst’s Event Handler system
Created in C++ for low resource consumption, fast attack detection, and rapid response
Major Modules
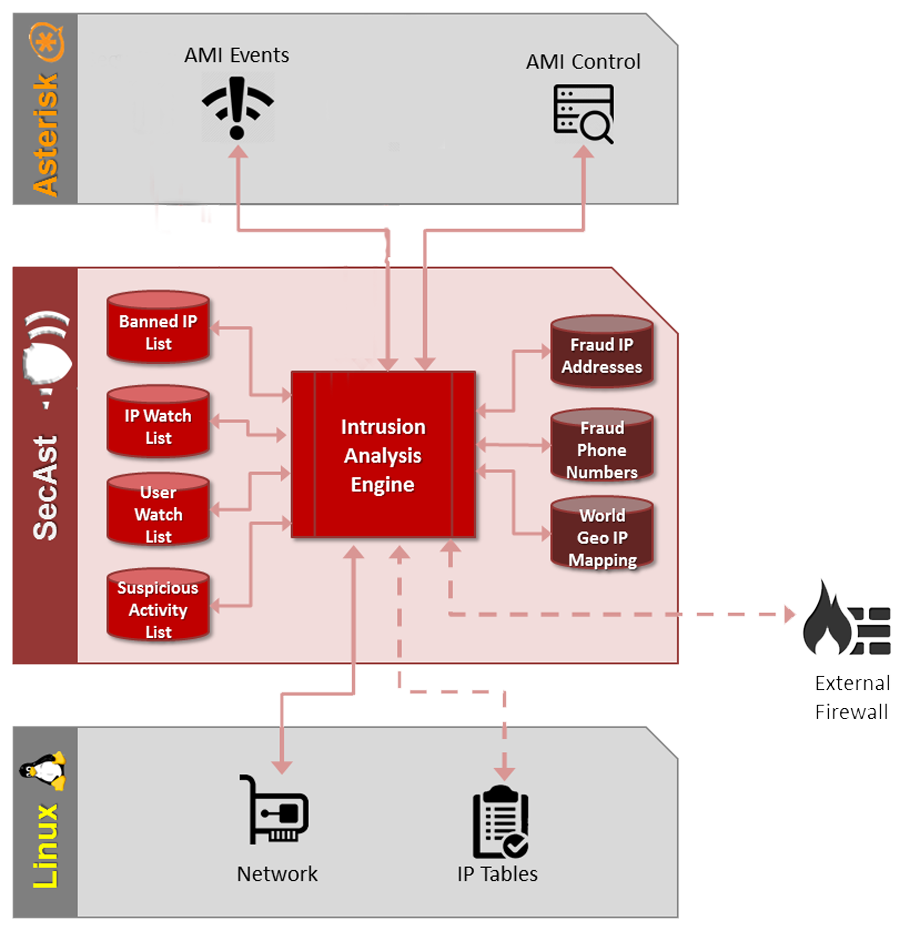
The Intrusion Analysis Engine is at the heart of SecAst, monitoring inputs from Asterisk, the operating system, behavioral history, and proprietary security databases. User and device activities are constantly being profiled looking for suspicious behavior and SecAst maintains risk scores for every existing connection and attempted connection. Based on administrator defined thresholds, SecAst will block or restrict activities of any user or device to ensure fraud is mitigated and hacking is prevented.
SecAst monitors network connections, attempted network connections, network traffic, device profiles and more. These inputs are derived from SecAst’s proprietary network sensors which continually feed data to SecAst. The Intrusion Analysis Engine uses these inputs to prevent a connection, flag a connection for further monitoring, or even detect unusual traffic patterns.
SecAst integrates deeply with Asterisk to monitor dialplan operations, and more specifically the behavior of individual connections. Data such as call setup frequency, dialing rates, etc. all serve as inputs to the Intrusion Analysis Engine.
A best practice common to computing environment hardening is to keep attackers off the internal network. SecAst offers an API to communicate with virtually any external firewall to block, unblock, and monitor undesirable IP addresses at the network edge. SecAst includes sample handlers for firewalls from Cisco, Mikrotik, pfSense, and more.