VoIP Honeypot Report 1
Results of Honey Pot Experiment #1
»
Overview
Telium placed a VoIP PBX (running FreePBX with Asterisk 14) onto a public IP for a period of 120 days. Telium’s SecAst security software was added to the PBX to track all attacks and provide the data presented below. SecAst was setup to block an attacker for the remainder of the experiment once their attack was recorded, so each attack represents a new (not-repeated) attack.
The primary purpose of this “honeypot” experiment was to assess the number and nature of attacks an administrator can expect against his/her server, without making public the server’s IP or any credentials. The secondary purpose of this experiment was to demonstrate the risk of exposing account credentials on the internet through chat/message posts, as automatic scraping of SIP account credentials is obviously taking place.
The experiment was divided into two phases: In the first phase (days 0-60) SecAst was setup to restrict endpoint access to North America only – to show the impact of GeoFencing. In the second phase (days 61-120) SecAst was setup to allow worldwide access, and a set of valid SIP credentials were published in 3 public forums allowing users to register with the server and make calls (which terminated automatically after 3 seconds).
Impact of GeoFencing
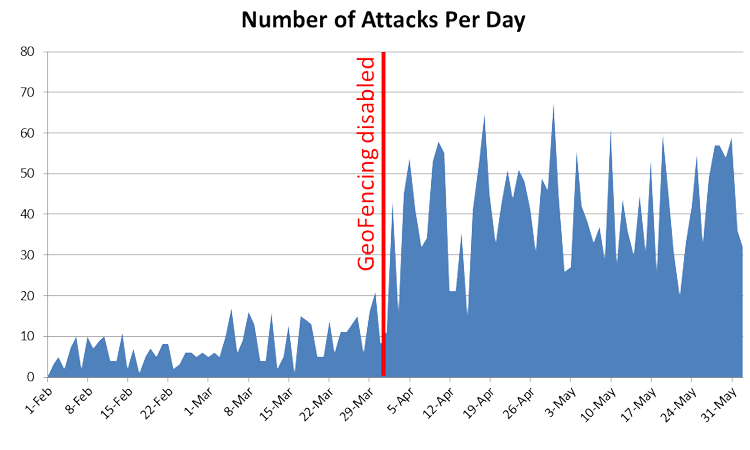
The graph to the right demonstrates the number of attacks against the PBX per day. Note that on day 60 GeoFencing was disabled resulting in a considerable increase in the frequency of attacks.
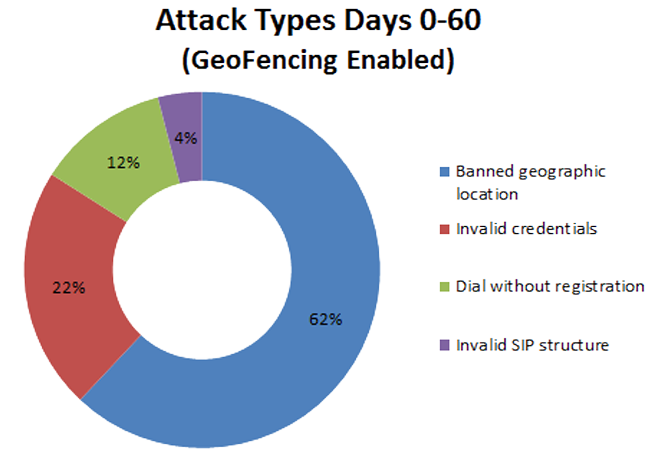
Attack Categories With GeoFencing
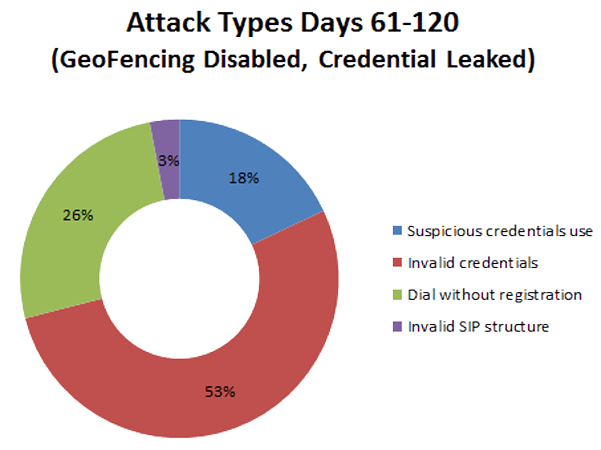
Attack Categories Without GeoFencing
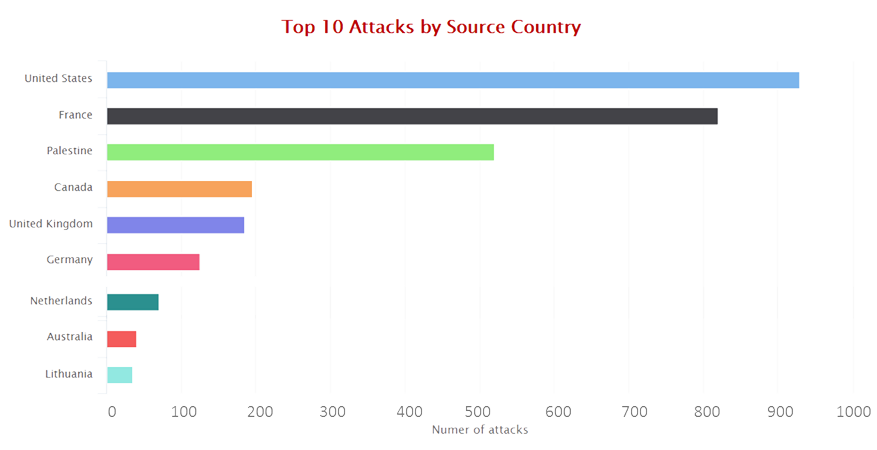
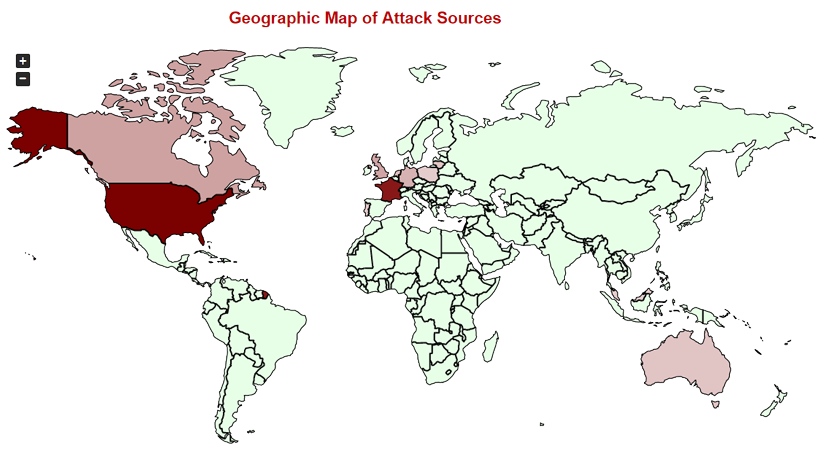
Attack Source Locations
Attack Intensity by Geographic Location