Security Databases
Easy to use hacking and fraud information specifically for telephony
SECDATA
»
TECHNOLOGY
Built for Telephony Fraud and Hacking Prevention
Identifies fraud and hacking unique to VoIP telephony
Realtime hacker IP and fraud phone number data to prevent zero-day attacks
Worldwide data capture identifies cross-continent fraud schemes
Simple REST interface provides instantaneous risk assessment
Major Modules
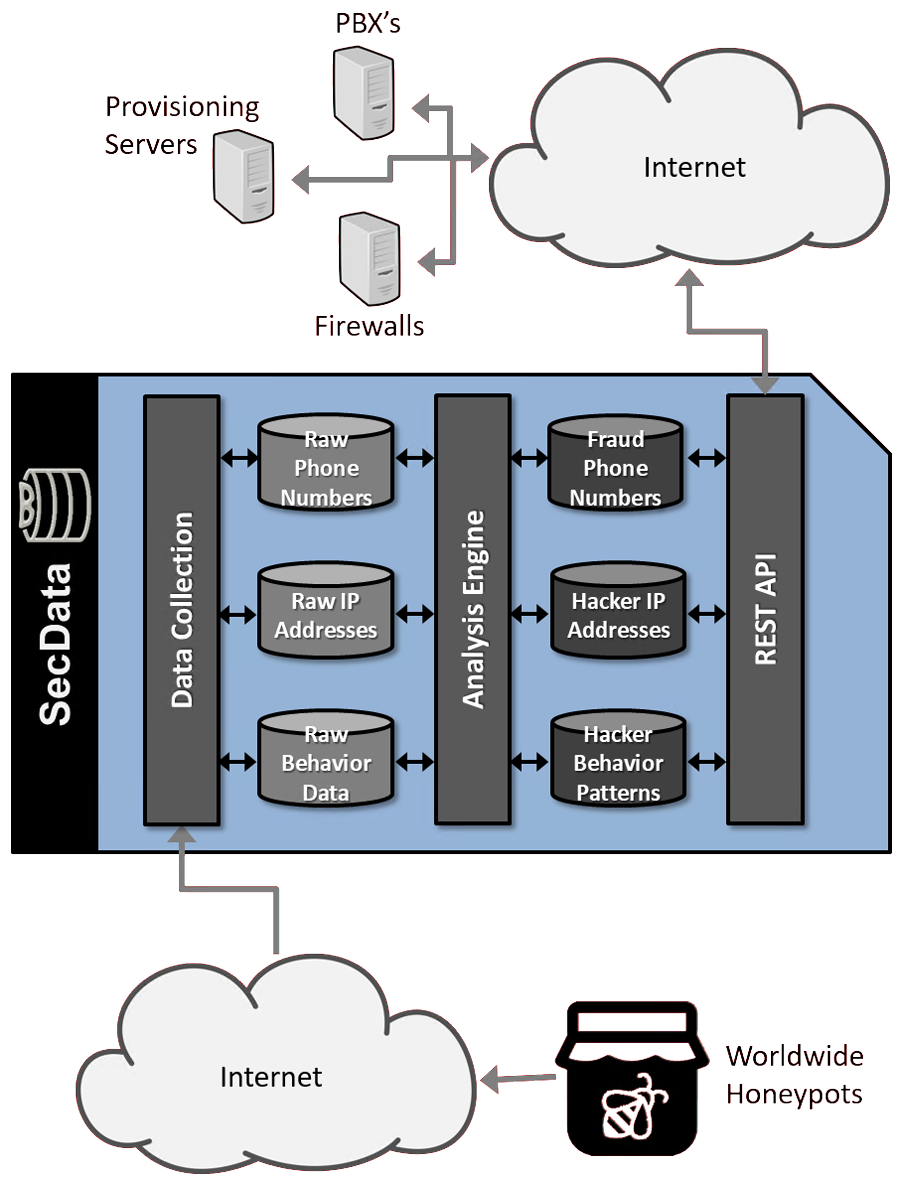
The Worldwide Honeypots are 15 exposed PBX’s (and related services) across the globe. These honeypots are designed to attract and monitor the activities of hackers and fraudsters, capturing behavioral data, recording their IP addresses, and noting any numbers dialed. The raw data is continually sent to the Data Collection module.
The Data Collection module accepts raw fraud, hacking, and intrusion behavior data from external data capture servers. The module stores all information in local databases for downstream analysis.
The Data Analysis Engine searches the raw information looking for patterns and relationships between data points. Where possible, it links related attacks and related source IP addresses to facilitate detection of new attacks. After analyzing all of the information in the raw databases, it appends new information to the Fraud Phone Number database, Hacker IP address database, and Hacker Behavior Patterns database. It also ages existing data and updates rules for computing risk scores.
The ReST API accepts queries from customers’ servers, and searches the security databases for relevant matches. It performs a series of calculations to create quantitative inputs for determining risk, and then computes a risk score from 0 (low risk of fraud/hacking) to 100 (high risk of fraud/hacking). Finally, the module formats a response in the requested structure, and sends the result to the customers.