VoIP Honeypot Report 2
VoIP PBX Honeypot Data Jan 1 2020 to March 20 2020
»
Overview
Telium operates numerous VoIP PBX’s (running either FreePBX, Issabel, Asterisk, or Telium PBX simulators) on public IP’s to collect VoIP hacking and fraud data (as part of Telium’s VoIP security service). In addition to gathering VoIP hacker and fraud data, these “honeypots” help gauge the number and nature of attacks an administrator can expect against his/her own PBX.
While these VoIP honey pots collect a large amount of security related data, this report focuses only on the number of attacks from January 1, 2020 to March 22 2020. The report defines an attack as an attempt to gain access to PBX resources without authorization, using a variety of recognized attack vectors. This includes not simply attempts to dial/register without credentials, but also malformed SIP packets, use of known SIP exploits, GUI exploits, attempted management interface connections, etc.
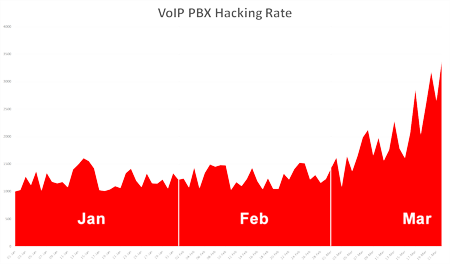
Number Of Attacks Per Day
The graph to the right shows the number of attacks against the PBX’s per day from January 1, 2020 to March 22, 2020. A significant increase in attack rate is apparent starting in early March 2020.