Forum Replies Created
-
AuthorPosts
-
in reply to: Migrating to NodePrep #17245
The alignment is only a small part of NodePrep does…but don’t worry, you can still customize the sync event handlers however you want.
i.e. we aren’t deprecating the syntax or event handler files.
NodePrep combines a lot of Call Continuity module functionality that would benefit the non-OEM editions, so we are slowly moving that functionality into the Flex and Unlimited editions.
in reply to: Rebuilding queues after failover on OEM edition #17208The “call continuity” module is responsible for rebuilding the queues on the standby server (as it promotes to primary). The queues are rebuilt in the order of which the calls arrived at the PBX. If a call was first answered by a user (or some other service) and then transferred to the queue, it is possible that the order of arrival at the PBX does not match the order of entry to the queue. Realistically, those few calls might be only slightly out of position.
At this time we do have any workaround for this situation. However, this should affect very few calls (<1%) and the impact should be minimal (minor change in order for those few calls). In a future version of the call continuity module we may use call queue entry times for queue reconstruction. Because of some Asterisk limitations this is not as easy as it sounds.
If this issues is a problem for your customers we recommend announcing estimated wait time instead of queue position.
in reply to: Corrupt AstDB file #17193First of all, make sure that HAast isn’t warning you of a real problem. Does your standby node have latency problems? Sever network/cpu/disk latency could easily cause a sync to fail. And if that’s a rare occurrence then that’s ok. But if it’s happening regularly then first check for hardware (or virtualization) issues.
Next, as you may already be aware, FreePBX is known to destroy the AstDB file for no good reason on rare occasions (i.e. it’s a bug that occurs rarely). See https://community.freepbx.org/t/corrupted-astdb-how-to-rebuild/4809 This problem has existed for many years customers have commented that Sangoma appears unable/unwilling/uninterested to resolve this. The nature of the problem is that Astdb file remains valid and whole (i.e. a valid SQLite 3 file), but critical information is missing or invalid in the database. Since HAast will try to apply changes to the AstDB upon sync, the sync may fail if the contents violate SQL relationship rules or other integrity constraints.
To pinpoint the cause, please enabled debug in the syncjob on the standby computer; for example, the file /etc/xdg/telium/haast.conf.d/asterisk.syncjob.conf might contain a syncjob called asterisk-db. Add the following line to that job:
asterisk-db/debug=on
And then restart HAast on the standby node. This will cause a detailed bug file to be created in the /var/tmp/haast directory. After a few automatic (or manual) starts of the asterisk-db sync job, please send that file to the support team and we will have more insight on what is going wrong.
In summary, the most likely cause is OUTSIDE of HAast. Experience has show that HAast will detect these errors and report them, but it doesn’t mean you have a HAast problem. If you are sure the hardware, Linux, and resources of the nodes are ok then starting debugging in HAast as described above.
in reply to: Withstanding penetration testing #17191If your cluster needs to withstand penetration testing (or the equivalent of exposing the management ports to the internet), then there are a number of steps you must take to harden your cluster.
1. Ensure you set complex id and passwords for the Asterisk management interface.
2. Set the Asterisk management interface to listen to localhost only.
3. Ensure you set complex credentials for HAast peerlink.
4. Protect the HAast GUI (https) interface with the htpasswd utility
5. Ensure you set complex credentials for rsync.
6. Ensure you set complex credentials for database(s) in use.
7. Limit database port access to localhost and the remote peer.
8. Set iptables rules to further limit interface/port combinations of the above to the peer and any trusted management workstations.
9. Set iptables connection rate rules to the max necessary for your cluster to operate.The HAast GUI and ReST interface can be disabled altogether if you do not need that functionality. Note that the GUI and ReST interfaces do not use ANY 3rd party libraries; it is all hand coded in PHP and tested for stability and security. However, it is possible to overload or find a weakness in Apache HTTPD; in which case disabling the GUI and ReST interface is recommended.
If you do not need direct access to the HAast telnet interface, then you should set the HAast telnet interface to listen to the localhost address only. Once that change is made, you must SSH to the node first and then telnet to HAast in order to access the interface.
HAast is designed to support even the most heavily loaded systems. However, HAast on it’s own is not designed to withstand loads/connection attempts beyond what can be found in a normal production environment. In other words, HAast is not meant to withstand the challenges of penetration testing or open internet access without first hardening the cluster. The above hardening recommendations do add additional load to the cluster nodes, so in general we do not recommend implementing the above unless you have a real need to harden your cluster.
in reply to: What to do after maintenance renewal #17189Thank you for renewing your maintenance. Once we have received payment we update our system to show the new term (duration) of your maintenance agreement. This allows our support team to continue providing you with support, generate replacement files if needed, etc.
If you wish we can also send you an updated license file (which shows the new maintenance term) to install on your system. However, this is optional. Most customers do not want to interrupt software operations just to show a new date, so you can safely skip this stop. However, if you chose to upgrade your software during the maintenance period we recommend that you request a new license file at that time.
Note: Your software will continue to operate just fine without installing the new license file. (Our licensing system shows the new expiry date)
in reply to: MySQL server has gone away #17050This error means that the connection to the database server has closed unexpectedly. HAast will immediately try to reopen the connection to recover, which is why you see data still being written to the database. However, the database operation that triggered the error has failed and it’s data will not be recorded (if it operation was trying to add data).
The root cause is that your MySQL/MariaDB server is configured to automatically close the connection after a period of inactivity, and that period is too short. To solve the problem, edit the MySQL configuration file (usually /etc/mysql/my.conf and add the following:
[mysqld]
wait_timeout = 31536000
interactive_timeout = 31536000in reply to: Where is the installation manual #17022We include the installation manual in the download package. Untar the HAast package you just downloaded and look in the /docs folder. You will see a file called detailed_installation_guide.pdf
The installation guide is over 100 pages in length, and takes you through all of the steps required to get HAast up and running.
in reply to: How to activate / request a license #17020If you have chosen USB Dongle activation, then there a few more steps required to pair your new dongle with your license. Once your dongle arrives plug it into the computer and restart the HAast service. Reconnect to the product’s telnet interface and issue the “license usbdongle” command. For example:
[root@pbx_qa_17:/usr/local/haast] $ telnet 172.31.224.14 3001
Trying 172.31.224.14…
Connected to 172.31.254.14.
Escape character is ‘^]’.
HAast telnet interface on ‘PBX QA 17’
HAast>license usbdongle
Your USB dongle has been detected but is not yet paired with your license.
To pair your USB dongle with your license send the following dongle ID to
support@telium.io to receive a pairing code :
5010-5473-C839-94B9
Copy the pairing code and paste it into an email to support@telium.io and include your license number. We will reply with an activation code that you must enter. For example:
When ready enter the pairing code below (or . to abort)
activation code>46A9-9907-43DB-4F06
Your activation code has been accepted. Please restart the HAast service to use the activated license.
Now exit the telnet session and restart the HAast service. HAast will restart fully licensed and you are ready to use your licensed product. You can also verify the license by repeating the “license usbdongle” command, and it should indicate that the dongle has been paired to your license. For example
[root@pbxqa17:/usr/local/haast] $ telnet 172.31.224.14 3001
Trying 172.31.224.14…
Connected to 172.31.224.14.
Escape character is ‘^]’.
HAast telnet interface on ‘PBX QA 17’
HAast>license usbdongle
Serial number: 3040504215618650775
Paired: yes, on Tue Jun 14 17:52:40 2022 EDT
Locked out: no
HAast>
in reply to: Running inside a container #17019Yes. HAast fully supports containers. Normally HAast will run inside the container with Asterisk; however, we have seen deployments where HAast runs on the host and starts a container (containing Asterisk) on demand.
If this is you first exposure to HAast we recommend installing HAast inside the container with Asterisk (and optionally a GUI).
Note: Due to excessive support incidents helping customers understand and setup containers, Telium has removed support for this topic. Customers are welcome to use containers, but the technical support team cannot answer questions about their setup, configuration, or use.
in reply to: Do you support IPv6 #16972All of the libraries and components used by HAast are IPv6 capable, and HAast is designed to accept IPv6 settings. However, due to lack of customer demand IPv6 functionality is not currently tested or certified.
You are welcome to try IPv6 settings with HAast and everything may work. However, we do not officially support IPv6 yet. As of May 2022 we have not had any customer need IPv6 (though a few customers have inquired).
If IPv6 is essential for your implementation Telium would undertake a (for fee) project to certify HAast (only the platform and architecture of HAast you are using). There is not enough overall demand to justify doubling the entire QA process indefinitely for IPv6.
If you are an OEM or volume license customer please contact your account manager to discuss your needs.
in reply to: Slow turnaround for integration project #16922I completely understand your frustration. However, even though you have been in discussions with your CUSTOMER for 6 months you have not included Telium in your plans (you did not give TELIUM 6 months lead time, you gave us 2 weeks). The equipment you ordered today must be shipped to us internationally, setup and tested, and then shipped to you. Our professional services staff (project engineers) staff are usually booked weeks ahead.
In the future you may wish to involve Telium in the process earlier, order equipment further in advance, and book Telium engineering time further in advance. We also recommend a 60 day burn-in period for all hardware before deployment (particularly for emergency services or mission critical systems). We are happy to do this for you, but this adds even more lead time to the project. Our VARs and integrators typically schedule projects to go live at least 90 days out to account for all of the lead times and uncertainties involved in a project. Giving Telium 2 weeks notice is just too short for what you are asking. In fairness the frustration you are experiencing is not because of Telium; it’s because something has gone wrong in the project plan well before you placed the order with Telium.
You are always welcome to contact your account manager, or escalate to our VP Engineering or VP Sales for help. We try very hard to exceed the expectations of our customers (and we have a stellar reputation to prove it). We will always do whatever we can to help.
in reply to: Move license between AWS servers #16835You have described two very different needs in your question, so I’ll try to answer them separately. If you choose Hardware Fingerprint activation on AWS, then your license is tied to your instance ID and MAC address. So you can safely move the instance between hosts (i.e. hypervisors, not guest VM’s), change instance size, etc. The license will remain activated (tied to that instance). You can safely start/stop the instance, just don’t ever delete it or delete the NIC as that will invalidate your license.
If you plan to have multiple AWS instances ready to start but will only use one at a time, then you should choose Cloud activation. Cloud activation is not tied to any (virtual/physical) hardware so whichever instance is running is the one that will use the license. However, do not start more than one instance at a time (i.e. don’t try to use a single license on multiple instances simultaneously) or that will invalidate your license.
I should point out that we use a third party license product, and they have no obligation to issue a new license once an existing one has been invalidated. In other words, if you invalidate your license you will most likely have to buy an entirely new license (full price). So plan your deployment carefully to avoid wasting a license. We have no ability to “un-invalidate” a license – we are at the mercy of the license vendor, and we understand their need to prevent license fraud as that’s the only way they can stay in business.
in reply to: Protecting plain text credentials in config file #16744The standard in Linux is to leave credentials in plain text config files, and then protect the files using file permissions (owner/group/world).
However, we realize there are some cases where even the administrator should not be aware of certain credentials so HAast includes a “key chain” feature where HAast can store certain configuration values in an encrypted file (called a keychain). Once a key (comprised of a name and value) has been added to the keychain its value cannot be viewed by the user; it can only be referenced by its name.
To use a keychain entry in the config file replace the value with the key name prefixed with @. For example, if the config file contains:
[peerlink]
secret=”MySecretPassword”It could be replaced with
[peerlink]
secret=@PeerLinkSecretNext you should add the key to the keychain, holding the value you wish to keep hidden:
[root@qa121]# telnet localhost 3001
Connected to localhost.
Escape character is ‘^]’.
HAast telnet interface on ‘QA121’
HAast>keychain add PeerLinkSecret
Enter the key value exactly as you want it to be stored.
key value>MySecretPassword
The value associated with key name [PeerLinkSecret] has been set
HAast>Then just restart the HAast service and your credentials will be protected by the keychain.
in reply to: Encryption of config file passwords #16546There are a few ways to address your problem.
First, you can limit access to the HAAst config files (or even entire /etc/xdg/telium directory) so that only the root user can read them. Using the chmod command will allow you to set these files to readonly (r – -) for root:
chmod 400 haast.confSecond, you can also encrypt the password before placing it into the config file. For example, using md5sum we can generate a hash of your obvious password:
[root@qa14 dev]# echo "MyObviousPassword" | md5sum 7f1e7328e9c668dbc73485eecd91b7ba -Then you would use 7f1e7328e9c668dbc73485eecd91b7ba as your password entered into the haast.conf file on both nodes.
Third, you can store sensitive config file information in the HAast keychain. To use a keychain value in a configuration item simply replace the value with @KEYNAME. Applicable configuration items show @KEYNAME as an option in the documentation. Note that a KEYNAME can contain only letters, numbers, and underscore, and case of the letters is ignored. See section 3.1 of the installation guide (as of Jan 2021) for further details of the keychain.
in reply to: Configuring second FreePBX node using HAAst sync #16504No! Unlike most of the other configuration generators, FreePBX does something a little unusual. Every time you add a module (or even upgrade a module) to your system FreePBX might change the structure of the database / add tables to hold the additional data.
So if you now sync from your primary node to your secondary node, settings would be lost because the associated tables/fields are missing on the secondary node. Conversely, if you now sync from your secondary node to your primary node, settings would be missing because the necessary source settings are absent. (See image below). This is why the HAAst installation guide and maintenance manual provide specific installation/upgrade instructions relating to FreePBX. Every year we have at least one customer that damages their FreePBX cluster because they did not follow the installation/maintenance guides.
Similarly, updating a module might change table structure, and that’s why we say to disable any automatic updates in FreePBX. Most other configuration generators are smart enough to detect a configuration mismatch between versions/modules, but FreePBX does not and will probably break (dialplan failure) unless the two nodes are kept identical (in terms of modules enabled/installed/versions).
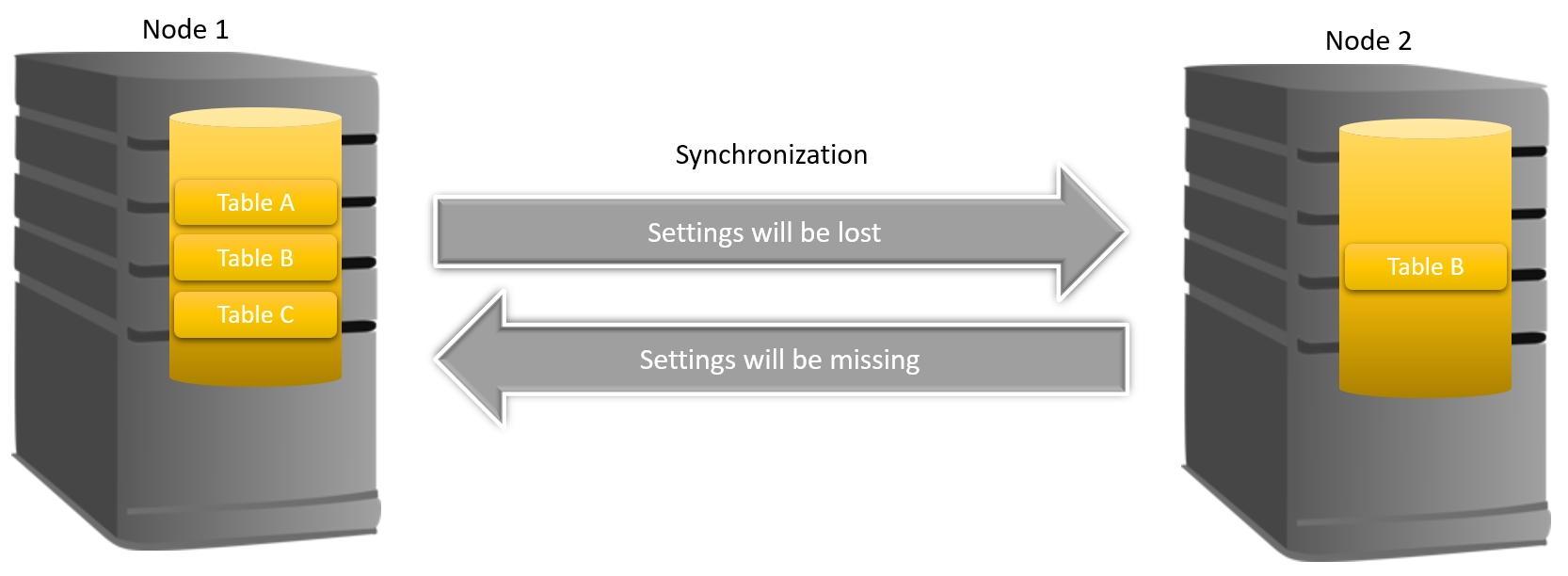
Even if HAAst were to copy the metadata (table structure) as well, you would still have problems since the PHP code which makes up FreePBX will not understand the settings (if the code version doesn’t match the settings version). This may result in the PBX failing to process calls as the dialplan crashes, and/or failure to configure, and/or failing to complete an APPLY button push.
To read more about how to properly setup your nodes with FreePBX see sections 3.6 and 10.1.5 of the Detailed Installation Guide, and sections 7 and 8 of the Maintenance and Operations Guide.
If you have already corrupted your FreePBX setup and your cluster won’t process calls (due to dialplan fialure) see this forum post
-
AuthorPosts

