Home › Forums › HAast (High Availability for Asterisk) › Configuration & Optimization › How to configure AWS based cluster for shared VoIP NIC › Reply To: How to configure AWS based cluster for shared VoIP NIC
First of all, AWS Lightsail has hidden access to some features that you will need to make this work, so you will instead need to setup a couple of EC2 instances. Since you want to share a VoIP NIC (shared IP) between nodes, your two nodes must reside in the same region but can reside in different Availability Zones (AZ’s).
Since (in most configurations) each node will have two IP addresses, and each address cannot be in the same subnet as the other (basic routing limitation), you must create 2 subnets within your VPC. If you want your two nodes to reside in separate AZ’s, then you will have to create 2 subnets per AZ (since subnets cannot span AZ’s). You might have to manually ad private IP(s) to NIC(s) in Linux depending on your design. You must then setup a security group encompassing both nodes, which allows SSH traffic into the management IP, and VoIP traffic in/out of the VoIP IP.
And finally you have some choices around how many NIC’s and public addresses your want in your setup. The more you want, the more complex the setup. We have created four basic designs you can chose from (but there are more):
- Dual NIC, Dual public IP
- Single NIC, Dual public IP
- Dual NIC, Dual Private IP, Single public IP
- Single NIC, Single Private IP, Single public IP.
The first option is the one we normally implement as it is easy to manage, separates traffic across NIC based on traffic type, avoid loss of management connection in case of VoIP IP issues, etc. But this is also the hardest to implement for AWS EC2 novices. As well, setting up routing rules can be a challenge for someone who doesn’t do network management as part of their job. We also prefer only a single VoIP IP (not dual public VoIP IP’s).
The fourth option is by far the simplest (almost trivial) to setup and you won’t have to worry about routing rules, but you will NOT have external access to the management IP’s of your nodes. To work around this you would either have to create a VPN into your VPC, or setup a third host whose sole purpose is to allow SSH relay to the internal hosts (management IP’s). We can also swap public IP’s between nodes if this makes life easier – to ensure continued direct external access to both nodes (but this is painful to use during setup).
Here’s an overview of the four designs:
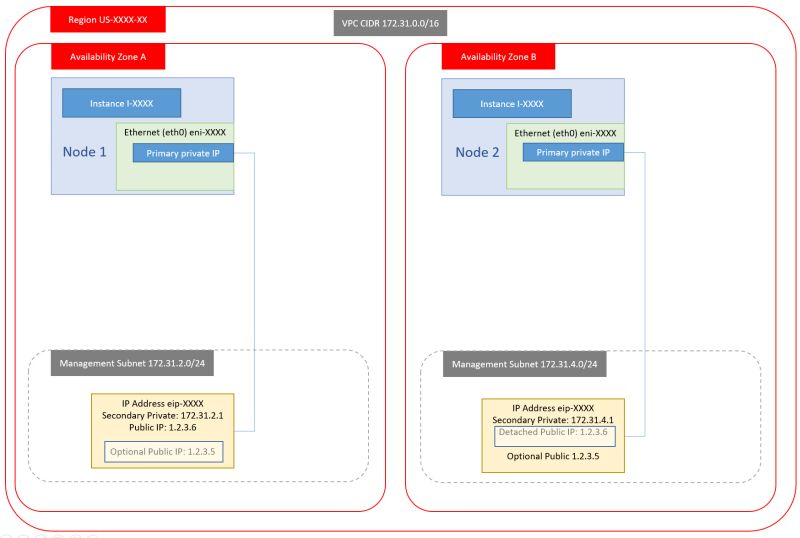
1. Dual NIC, Dual public IP
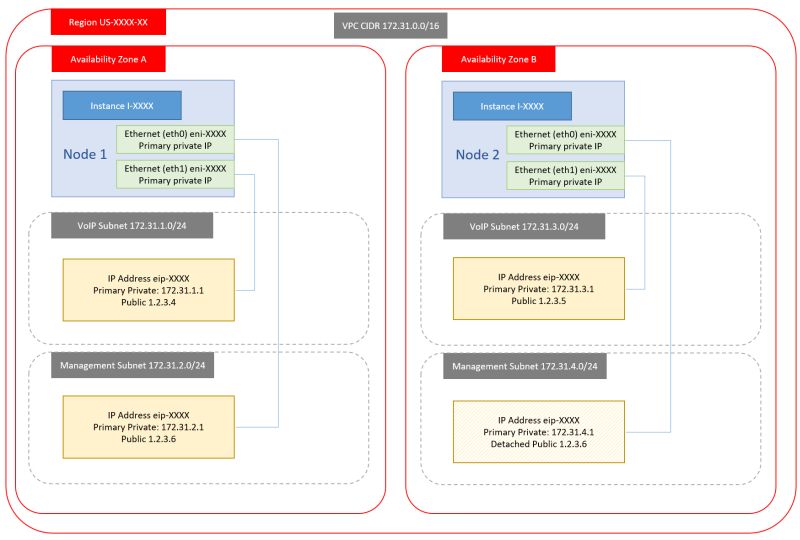
2. Single NIC, Dual public IP
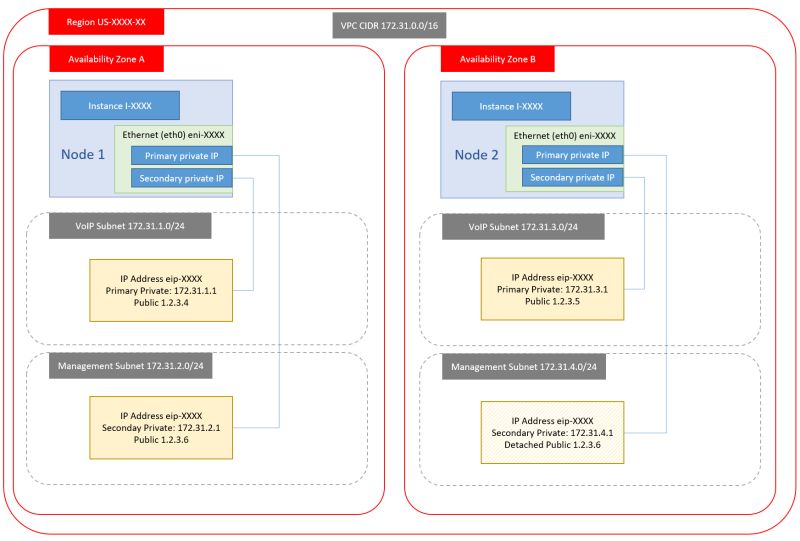
3. Dual NIC, Dual Private IP, Single public IP
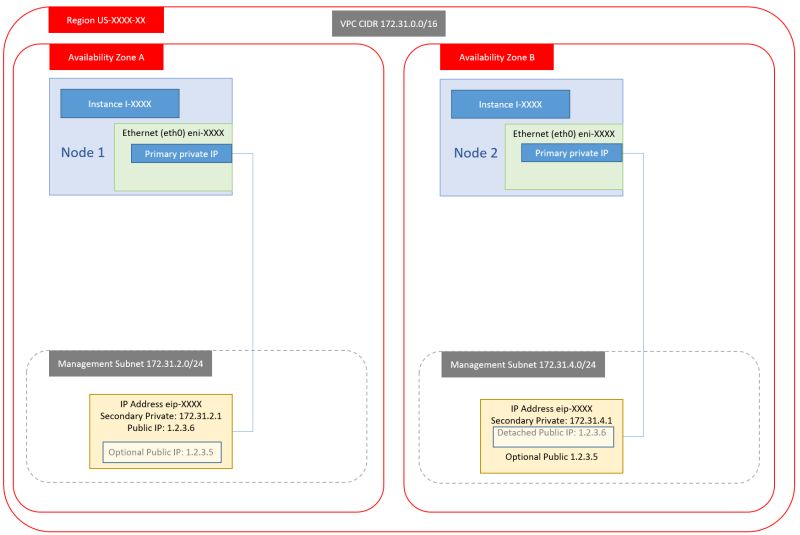
4. Single NIC, Single Private IP, Single public IP